The Therapist’s Full Guide to Data Compliance (UK)
A Comprehensive Step-by-Step Manual for Counsellors
By Samantha Newport.
As counsellors and psychotherapists, we handle some of the most intimate and sensitive information that clients can share. Protecting this data is not only a legal and ethical obligation under the UK GDPR, ICO guidance, and BACP Ethical Framework - it’s also a critical element of maintaining client trust and professional integrity.
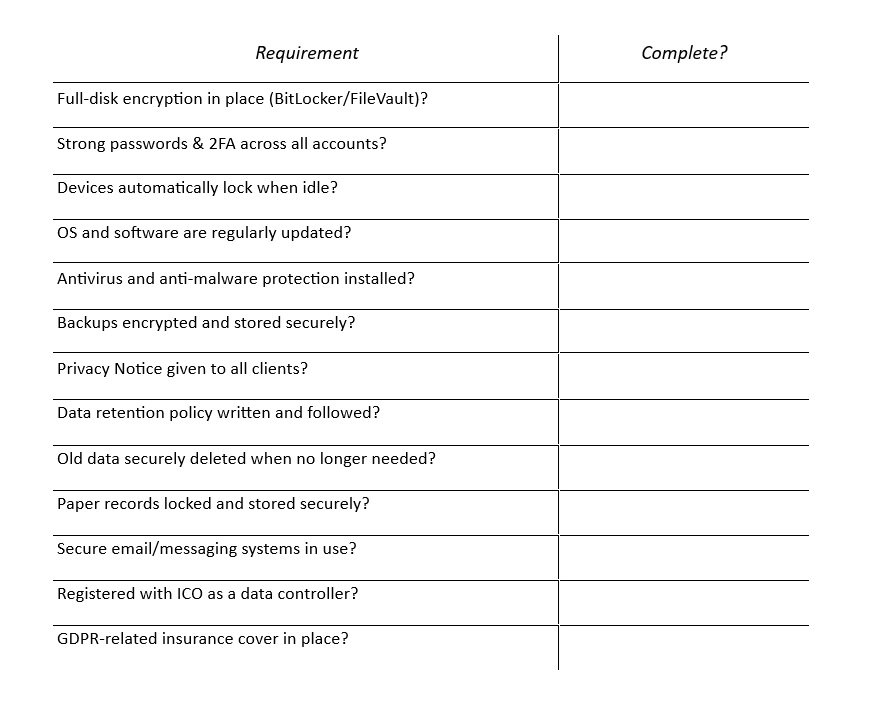
To protect client information on your laptop or PC, and ensure compliance, you need to implement strong technical, organisational, and procedural measures. This article – or practical guide - details a comprehensive and compliant checklist tailored to UK counsellors, followed by the risks of non-compliance.
This guide is designed to be:
A whistle-stop tour of clear, detailed practice for new and seasoned counsellors wanting to learn more about how to be security compliant, as well as how to navigate the often-confusing technical aspects;
A how-to manual for implementing digital and paper-based compliance;
A preventative toolkit to protect you and your clients;
Suitable for use in solo private practice, partnerships, or agency work.
Device Security & Data Encryption
Encryption is a method of protecting data by converting it into a coded format that can only be read or accessed with the correct password or key. For counsellors handling sensitive client information, encrypting your PC or laptop ensures that, if the device is lost, stolen, or accessed without permission, the data remains unreadable and secure. Under GDPR and ICO guidelines, encryption is a critical safeguard - it helps fulfil your legal obligation to protect client confidentiality and prevents potentially devastating data breaches.
Next, this guide will walk you through exactly how to encrypt your devices - whether you're using a Windows PC, a Mac, or alternative systems. You’ll learn which built-in tools (like ‘BitLocker’ for Windows and ‘FileVault’ for macOS) are available, how to check if your device is compatible, and step-by-step instructions for enabling encryption.
For those without access to these tools, we’ll also recommend trusted third-party options to ensure your client data remains protected, compliant, and secure across all platforms.
Windows Devices – Using BitLocker
What is BitLocker?
‘BitLocker’ is built-in full-disk encryption for Windows Pro, Enterprise, and Education editions. It prevents unauthorised access to your hard drive if your laptop is lost or stolen. It’s a must-have for GDPR compliance if you're storing sensitive data like counselling notes.
Requirements:
Windows 10/11 Pro, Enterprise, or Education (upgrade through the online ‘Microsoft Store’ if you do not have this. E.g., you have ‘Windows 11 Home’);
TPM chip (Trusted Platform Module – built into most modern laptops).
How to Check Compatibility (i.e., if your version of Windows has/can have BitLocker):
Press the ‘Windows’ symbol + ‘R’ key (both on your key board), together. A pop-up box will come up, titled ‘Run’;
Type in ‘msinfo32’ into the typing area of this pop-up. Then press ‘Ok’;
A new pop-up box will appear, titled ‘System Information’. Under 'OS Name' (the first item listed in this new pop-up box) you’ll see the version of Windows that you have (e.g. ‘Windows 11 Pro’ or ‘Windows 11 Home’);
Under 'System Summary', check 'TPM' presence under 'Security'.
Note: BitLocker requires Windows Pro or higher. If you see Windows Home, BitLocker won’t be available.
Step-by-Step - How to Turn On BitLocker:
Open your PC/Laptop’s ‘Start Menu’ > search for ‘Manage BitLocker’ by typing it into the search bar in the start menu;
The ‘BitLocker Drive Encryption’ window will open. Click ‘Turn on BitLocker’ for your C: drive;
Choose unlocking method: password or USB key
Save your Recovery Key securely (not on the same device) - you’ll need this if you forget your password! Either:
Store on an encrypted USB;
Print and store in a locked cabinet;
Save to secure encrypted cloud (e.g. ‘Proton Drive’);
5. Choose to encrypt entire drive (better for existing data, otherwise device will only be partly encrypted);
6. Select ‘New encryption mode’ (better for modern devices);
7. Click ‘Start Encrypting’ (or similar wording suggesting confirmation);
8. Let it run (15-45 mins). You can still use your device during this.
After Setup:
BitLocker runs silently in the background;
No need to manually re-encrypt;
If stolen, no one can access data without your password or recovery key;
Your files and client data are safe and compliant with GDPR’s ‘Security of Processing’ requirement.
If You Don't Have BitLocker:
Upgrade to Windows 11 Pro (approx. £119) via Settings > System > Activation
Or use third-party encryption tools (see further into guide).
Encrypting Client Files
For individual client files (Word documents, Excel spreadsheets, PDFs), another layer of protection must be put in place:
Word Documents: Use the ‘Encrypt with Password’ feature (open your document and select ‘File’ > ‘Info’ > ‘Protect Document’ > ‘Encrypt with Password’). This encrypts the file and requires a password to open, ensuring client confidentiality.
PDFs: Use tools like ‘Adobe Acrobat’ to encrypt and password-protect PDF files, preventing unauthorised access.
When using Word or PDF’s built-in encryption features, the file is actually encrypted, not just password-protected. This means that even if the file is accessed, it cannot be opened without the correct password, keeping your client data secure.
Folder-Level Protection (Optional)
For added security, you can encrypt entire folders of files using tools like 7-Zip or WinRAR. These allow you to create encrypted archives with passwords, ensuring that all files inside the folder are secure.
MacOS Devices – Using FileVault
What is FileVault?
‘FileVault’ is full-disk encryption for macOS (10.10 Yosemite and later). ‘FileVault’ encrypts your entire hard drive (just like ‘BitLocker’), so if your Mac is lost or stolen, no one can access your client files without your password or recovery key. It's a must-use feature for counsellors holding sensitive data under GDPR, ICO, and BACP rules.
How to Enable FileVault:
Go to Apple Menu > System Settings > Privacy & Security;
Click ‘Turn On FileVault’;
Choose unlocking method (usually your login password);
Save your Recovery Key. Either:
Write it down and store in locked cabinet
Save in secure encrypted cloud storage
Optional: store in iCloud (less secure);
Restart your Mac to begin encryption (runs in background).
What Happens After?
Every time your Mac starts up, it requires the user password to unlock the disk;
The entire disk is encrypted, meaning even if someone removes your hard drive, they cannot access the files;
‘FileVault’ runs silently in the background — no ongoing management needed.
Best Practices for macOS:
Use a strong admin login password;
Keep your Recovery Key somewhere offline and secure;
To turn on auto-lock: System Settings > Lock Screen;
Use encrypted ‘Time Machine’ backups.
Sample Privacy Policy Line:
"All digital client data stored locally is protected with full-disk encryption (FileVault), in accordance with GDPR and ICO standards."
Third-Party Encryption Tools (If BitLocker/FileVault Not Available)
If you don’t want to/can’t upgrade so to access ‘BitLocker’, or something else means you cannot access this or ‘FileVault’, consider one of these GDPR-safe alternatives:
‘VeraCrypt’ is highly recommended for tech-savvy users, but setup is more complex than ‘BitLocker’.
Strong Passwords & 2FA
Creating Strong Passwords
At least 12 characters;
Mix of upper/lowercase, numbers, and symbols;
Avoid personal info, repetition, dictionary words
Example: Waffle9@SwimmingP00L#River!
[NOTE: This is a fake made-up password for the purpose of providing an example];
Never share any of your passwords.
Use a Password Manager:
If you find it hard to remember complex passwords, a password manager will help you generate and securely store strong passwords. This way, you only need to remember one master password.
Some good options: ‘1Password’, ‘Bitwarden’, ‘NordPass’
Stores and generates unique passwords
Use one strong master password only
Enabling Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security by requiring you to verify your identity in two ways: your password and a second factor (e.g., an app or a text message).
Recommended 2FA Tools:
‘Authy’ or ‘Google Authenticator’ for time-based codes;
Avoid SMS-based 2FA due to SIM-swapping risks.
Enable 2FA On:
Microsoft Account: https://account.microsoft.com/
Google: https://myaccount.google.com/ > Security > 2-Step Verification
Apple ID: System Settings > Apple ID > Password & Security
Social Media, Banking, Email, and Cloud Platforms
Save Backup Codes:
Store offline or encrypted.
Extra Tips for Strong Passwords and 2FA
Never share your passwords. Don’t send them via text or email, and always use secure means (password manager) to share them if needed;
Use a backup method for 2FA. Many services give you backup codes in case you lose access to your phone. Save these in a secure place (offline or encrypted);
Regularly change your passwords. Change them every 6-12 months, especially if you think an account has been compromised;
Avoid reusing passwords. Use a unique password for each account to minimise the risk of a single breach affecting multiple services;
Enable 2FA for everything. Enable 2FA for all apps that support it - your email, cloud storage, financial accounts, and social media.
Software & System Updates
Keep Your OS Updated
Windows: Settings > Update & Security > Windows Update
macOS: System Preferences > Software Update
Keep All Software Updated
Browsers: ‘Chrome’, ‘Firefox’, ‘Edge’ auto-update—check manually to confirm
Microsoft Office: File > Account > Update Options > Update Now
Antivirus & Anti-Malware
Built-in: ‘Windows Defender’ (adequate);
Third-party: ‘Bitdefender’, ‘Kaspersky’, ‘Malwarebytes’ (recommended for deeper scans);
Only run one antivirus at a time to avoid conflicts.
Data Storage, Back-ups & Minimisation
Data Minimisation
Only collect data necessary for your counselling work;
Delete notes/emails not required for record-keeping or ongoing care.
Secure Storage
Use encrypted folders or GDPR-compliant case management systems (e.g., ‘Bacpac’, ‘WriteUpp’);
Don’t store files on Desktop or unprotected folders.
Backups
Use encrypted cloud storage (e.g., ‘Tresorit’, ‘Sync.com’, ‘Proton Drive’);
Or encrypted external hard drive (don’t use standard USBs);
Never use unconfigured ‘Google Drive’ or ‘Dropbox’ for sensitive client data.
Documenting Compliance
Privacy Notice
Give every client a privacy notice explaining:
What data you collect & why;
How it’s stored & for how long;
Their rights (access, deletion, correction, etc.).
Data Protection Policy
Keep a written data protection policy explaining how you handle data securely.
Have a policy that outlines:
Devices used;
Encryption steps;
Backup procedures;
Retention & deletion schedule.
Record of Processing Activities (ROPA)
For most sole practitioners, this is optional, but it’s good practice to keep a simple record of:
What data you collect;
Where it's stored;
Who can access it;
How/when it’s deleted.
Confidentiality & Access
Only you should have access to client files;
Avoid sharing your laptop or leaving it unattended in public or shared spaces;
If disposing of the laptop, securely wipe the hard drive first.
Training and Awareness
Stay updated on ICO guidance and BACP ethical framework;
Consider taking GDPR training (e.g., ICO’s resources or CPD-accredited courses for therapists).
Secure Communications
Use end-to-end encrypted email (e.g., ‘ProtonMail’) or secure messaging platforms if communicating electronically;
Don’t send identifiable client data over standard email without encryption.
Final Tips
Register with the ICO (as a data controller) – it's a legal requirement for most counsellors;
Check your insurance covers GDPR breaches or data loss;
Regularly review your policies and update them annually or when practices change.
Retention & Data Deletion
In the UK, the retention of client data for counsellors, including contracts, referral forms, assessment information, and contact details, is governed by both GDPR (General Data Protection Regulation) and ethical guidelines set out by professional bodies like the BACP (British Association for Counselling and Psychotherapy).
GDPR states that personal data should only be retained for as long as necessary to fulfil the purposes for which it was collected. For healthcare-related records (which includes counselling and psychotherapy), it’s generally recommended to retain records for at least 6 years after the end of the therapy or the last contact with the client. In the case of adults, this aligns with the limitation period for bringing claims for personal injury, where the data may be required as evidence. For minors (under 18), records should typically be kept until the client reaches the age of 25.
The ‘BACP Ethical Framework’ and ‘Good Practice in Action’ suggest that counsellors should retain records for a minimum of 6 years for adult clients after the last session. Other sources, such as the BABCP states 7. For minors, the BACP states that records should be kept until the client reaches 25, as this is when legal claims could potentially arise (given that clients cannot sue before reaching adulthood).
Standard Retention Periods
Adult clients: 7 years after final session (check with your ethical body and/or ICO directly, as this number varies depending on where you look)
Minors: Until they turn 25 years old
Financial records: 6 years (for HMRC purposes)
Secure Deletion
Paper: Shred thoroughly (cross-cut or professional service)
Digital: ‘Secure erase’ (not just delete)
Tools: ‘Eraser’ (Windows), ‘Permanent Eraser’ (macOS)
Data Deletion on Request
Clients may request early deletion, but you should always inform them of the potential impact (i.e., if they need the data for a future legal matter);
Assess legal/ethical implications first;
Document the request and your actions.
What Happens if You Keep Data Too Long?
Holding data longer than necessary without a clear and justifiable reason can be a violation of GDPR principles. This could lead to complaints or even fines from the ICO.
Best Practice:
Create a ‘Data Retention Policy’: Ensure you have a clear policy for data retention and deletion that is in line with GDPR and professional guidelines;
Secure Data Disposal: When you dispose of records (after the retention period), make sure they are destroyed securely, whether in paper or digital form (e.g., shredding paper records or securely wiping electronic files);
Document Decisions: If you decide to keep records beyond the usual retention period for specific reasons (e.g., ongoing legal concerns), document why.
Paper Records
Paper notes and client details can still be kept in a GDPR-compliant, ICO-compliant, and BACP-compliant way, but there are strict rules around how you store, handle, and process paper-based data. The same principles that apply to electronic data also apply to paper records, and it’s important to implement strong safeguards.
Here's a breakdown of the steps you should take to be fully compliant for paper-based client notes and details:
Storage
Locked filing cabinet (flood proof and fireproof);
Only you (or trusted individuals with explicit access) should have the keys or access codes to those storage areas;
Avoid labels with full names;
Keep in a dedicated room or locked drawer.
Handling
Transport in sealed folders/envelopes;
Never leave files in cars or public places;
Store only what’s necessary.
Disposal
Retention same as digital (after 6-7 years for adults / age 25 minors);
Shred securely.
Secure Communication
Email & Messaging
Use ‘ProtonMail’ or other end-to-end encrypted email;
Don’t send identifiable data over unencrypted email;
Consider secure messaging tools: ‘Signal’, ‘Threema’, or encrypted practice portals.
Contact Forms
Ensure your website contact form is SSL-secured;
Avoid including personal identifiers in email notifications.
Complaints, Breach’s & Consequences
Would Anyone Find Out If You Didn’t Comply With The Rules?
The short answer: Not unless something goes wrong.
The ICO is the UK’s data protection authority and monitors compliance with GDPR. In general, they don’t go around checking individual practitioners for compliance unless there's a complaint or a data breach. If a client feels their data has been mishandled, or if there’s a security incident (e.g., a breach of client confidentiality), they can file a complaint with the ICO or raise it with you, directly. The ICO might then investigate the issue. This is why trust and confidentiality are at the heart of your profession.
While it’s rare for the ICO to conduct random audits of individual practitioners, they can investigate if a complaint is made or if a data breach occurs. If your practices were found lacking, they could issue fines or enforcement actions, including requiring corrective measures and even criminal charges in extreme cases.
Data breaches that involve significant financial or reputational damage (e.g., if your data handling practices were negligent and resulted in a major leak or misuse) could attract media attention or go viral, especially in today’s interconnected world. This could prompt public scrutiny, and if the ICO is alerted, they might investigate.
The BACP sets ethical and professional standards for its members. While they do have ethical audits and complaints processes, they’re more likely to get involved if a complaint has been filed against a member or if there’s a violation of their code of ethics (e.g., breaches of confidentiality or data protection mishaps). BACP would be especially concerned if there was a formal complaint involving a member's mishandling of sensitive client data.
Would an Audit Ever Happen?
An audit by the ICO or other bodies (like BACP) could occur in certain circumstances:
Complaint-driven audits: If a client or a third-party reports a breach or misconduct, it could trigger an ICO investigation;
Data breach: If you experience a data breach that affects your clients' personal data (e.g., data is leaked, hacked, or accessed by unauthorized people), and you report it to the ICO, the ICO might investigate how your data protection processes were managed;
BACP monitoring: The BACP might carry out spot-checks or investigate issues related to professional conduct, but this is more likely if there’s a formal complaint about ethical or confidentiality issues. BACP's focus is more on ethics than legal compliance, though both overlap.
How Many Counsellors Don’t Pay Due Diligence?
It’s tough to say, but likely more than you’d think. Many practitioners, especially those who are self-employed or solo practitioners, can feel overwhelmed by the amount of paperwork and rules. They might:
Not keep track of GDPR guidelines as strictly as they should;
Avoid proper data retention policies or client records management due to a lack of resources or knowledge;
Not stay up-to-date with the latest cybersecurity or privacy best practices.
However, BACP, ICO, and GDPR compliance are professional responsibilities, and failing to comply can lead to significant risks - including legal action, loss of reputation, and financial penalties.
How Can You Stay Protected?
If you’re doing your due diligence, you’re actually protecting yourself, your clients, and your practice from potential risks. It can feel like a lot to keep track of, but it’s ultimately about building trust and safeguarding sensitive information.
Here are a few things to help stay on top of things:
Regularly review GDPR guidelines: Stay updated on ICO regulations and BACP guidelines by subscribing to their newsletters or following their updates;
Maintain a professional record: Keep a detailed audit trail of how data is stored, accessed, and deleted. Documenting your policies and practices is essential in case of any complaints or audits;
Privacy and Data Protection Policy: Make sure you have a solid, clear privacy policy and client consent forms that inform your clients how their data is handled, retained, and stored.
If you ever get audited by the ICO, being able to show that you’ve actively taken steps to comply with data protection laws - like keeping records of client data for the required period, using encryption, and following proper protocols - will help show that you’ve done your due diligence.
How Would You Know If There Was a Data Breach?
Unexpected Activity or Suspicious Login Attempts: Unusual logins or login failures, like password changes you didn’t initiate or login attempts from unfamiliar locations or devices, could be red flags that your account or client data has been targeted. You may get notifications about login attempts or password changes from services like Outlook, Microsoft, or other online accounts (e.g., Google, Dropbox) you use to store client data.
Unfamiliar Communication: If you start receiving suspicious emails or messages that don’t align with your usual communication (e.g., phishing emails that seem like they’re coming from clients, but look odd or contain strange links), that’s a sign your email or account might have been compromised.
Technical Indicators: If you notice your computer running slowly, strange behaviour on your laptop, or programs being opened that you didn’t initiate, this could be a sign that malware or spyware has been installed on your machine to monitor or steal data.
Unusual file access: If certain files seem to have been accessed or edited without your knowledge, it could indicate someone has gained unauthorised access.
External Alerts: If a cloud storage provider (e.g., Dropbox, Google Drive) or a password manager you use notifies you of security issues, such as unusual access or a breach involving your data, that’s a strong indicator that something has happened. If you store client files on a third-party service that has a breach (e.g., a service you use for encrypted storage), you should be notified immediately. These companies have obligations under GDPR to inform you of breaches.
Audit Logs: Some data management systems you use (whether for client notes or case management) may have audit logs that track who accessed certain files and when. Regularly checking these logs could help you spot unusual access or behaviour. If you have access control systems or password-protected files, you should be able to see logs of who accessed them and whether there’s anything unusual in terms of time, location, or repeated failed attempts to access the data.
Communication from the Breacher: Sometimes, if you’re targeted by a hacker or attacker, they may directly contact you after a breach, demanding ransom (as in ransomware attacks) or asking you to pay for the return of data. This is rare but can happen.
Steps To Take Immediately if You Detect a Breach:
Contain the Breach: If you detect a breach (e.g., unauthorised access to your files or accounts), immediately change your passwords, lock accounts, or even disconnect devices from the internet if necessary to stop the attack. Alert clients if their data may have been compromised and tell them what steps you are taking.
Notify the ICO: As a data controller, if the breach involves personal or sensitive data and is likely to cause harm to clients, you must report the breach to the ICO within 72 hours.
Review Your Data Protection Measures: Conduct a full investigation into how the breach happened, and then review your security protocols. What failed? Was it weak passwords? Lack of encryption? An unsecured device?
Document Everything: Keep a record of everything: how the breach was discovered, actions taken, and how you informed affected individuals. This is part of GDPR compliance and also shows that you are taking responsibility.
Client Communication: Notify clients if their data was exposed or accessed. Be transparent about what happened, the potential impact, and the steps you’re taking to address it. This helps maintain trust.
The Dark Side of Data Protection in Therapy Practices
For many counsellors, doing the right thing is a top priority, driven by a sense of responsibility and fear of the consequences of failing to comply with data protection laws. However, the reality of compliance can be murky, especially in the context of independent therapy practices. Many counsellors may fear that breaches of data protection happen far more often than they should. When there’s little to no external monitoring or periodic audits, incidents can easily slip through the cracks - unnoticed and unaddressed. This is particularly concerning because, without clear oversight, breaches are often only detected if a client notices something unusual or the counsellor reports it. However, these incidents often remain undiscovered, suggesting that many breaches likely go unnoticed.
The existing system relies heavily on self-reporting and external triggers for identifying data breaches. This can create significant gaps, where breaches go undetected for long periods. If a counsellor doesn’t notice an issue and the client doesn’t raise any concerns, there’s little chance that the breach will come to light unless:
A wider investigation into related issues uncovers the breach;
The client notices something suspicious and asks questions (though this is often not the case);
The breach leads to financial loss or identity theft, prompting external investigations.
Without regular external oversight or audits, independent practitioners face a greater risk of undetected breaches. The reality is that many breaches likely go unnoticed. With thousands of therapists in the UK, it’s highly unlikely that any regulatory body, like the ICO, could monitor every individual practice.
The Challenges With The Current System
Reliance on Self-Regulation: Regulatory bodies such as the ICO rely heavily on self-reporting for breaches. They typically discover breaches only when a client files a complaint or when a third-party, such as an insurance company or email provider, flags suspicious activity.
Low Probability of Discovery: Due to the sheer volume of independent practitioners, it’s improbable that regulators will conduct regular checks on each individual counsellor’s data protection practices. Authorities generally focus on larger, more high-profile breaches, leaving smaller-scale issues under the radar.
Human Nature: The reality is that many people are complacent when it comes to small risks that don’t have immediate consequences. Counsellors, like anyone else, might neglect certain best practices - such as ensuring strong passwords, encrypting data, or securing devices - until something goes wrong. Without clear signs of a breach, there may be little incentive to take preventive measures.
Resource Limitations of Regulatory Bodies: Regulatory bodies such as the ICO do not have the resources to proactively audit every small business or sole practitioner. Their focus tends to be on large-scale breaches or high-profile institutions, leaving smaller practices with less direct oversight.
The Unlikely Event of Discovery
In the rare event that a breach occurs, the likelihood of it being discovered is slim unless:
A client notices an issue with their data or its misuse;
Regulatory authorities are tipped off or identify suspicious activity, such as fraud or identity theft;
A third party, like an insurance company, flags the breach due to related claims or issues.
Without direct complaints or investigations, the chances of a breach coming to light are minimal. However, the legal requirement to report remains in place, and failure to report could lead to severe consequences if the breach is discovered later on.
The current system heavily relies on trust and individual responsibility, leaving many breaches undetected unless the practitioner makes a mistake or fails to follow the necessary protocols. Without external audits or oversight, breaches can easily slip through. However, the consequences of failing to report a breach are significant.
If a breach is uncovered and it turns out the counsellor failed to report it, the consequences could be far worse than if the counsellor had simply adhered to best practices from the start. This puts those who do not comply with data protection regulations at risk of legal and professional repercussions.
The Ethics of GDPR Compliance
While the likelihood of a breach being discovered may seem low, counsellors have an ethical responsibility to remain vigilant. Even if most breaches go unnoticed, adhering to the required data protection protocols ensures that clients’ personal information is protected and that the counsellor’s professional reputation remains intact.
In the world of therapy, where counsellors handle highly sensitive information, it’s essential to take all necessary precautions. Ering on the side of caution and consistently following data protection regulations not only builds client trust but also ensures that counsellors can sleep easy knowing they’ve done everything possible to protect their clients’ privacy.
The risks of non-compliance may appear small, but when sensitive client data is involved, it’s better to be overly cautious than to risk potential harm down the line.
Even if the ICO or BACP never knocks on your door, your clients trust you to handle their personal data with the same care you give their wellbeing. That trust is your foundation.
Secure it. Maintain it. Honour it.